CaryptosHeadlines Media Has Launched Its Native Token CHT.
Airdrop Is Live For Everyone, Claim Instant 5000 CHT Tokens Worth Of $50 USDT.
Join the Airdrop at the official website,
CryptosHeadlinesToken.com
CaryptosHeadlines Media Has Launched Its Native Token CHT.
Airdrop Is Live For Everyone, Claim Instant 5000 CHT Tokens Worth Of $50 USDT.
Join the Airdrop at the official website,
CryptosHeadlinesToken.com
MetaMask is a popular software wallet that is designed for Ethereum tokens and decentralized applications (dapps). It operates on an open-source model, allowing users to access their cryptocurrencies and NFTs securely. Many users find MetaMask to be a safe choice for managing their digital assets, but understanding its security features is essential for anyone considering its use.
A central aspect of MetaMask’s security is its self-custody approach, which means users control their private keys. This wallet integrates with hardware wallets, which adds another layer of protection against hacks and phishing attacks. By utilizing passwords and privacy settings, MetaMask aims to keep user assets secure in the evolving landscape of crypto.
For those new to cryptocurrency, questions about safety can be daunting. It’s crucial to explore how MetaMask safeguards user data and the possible risks involved in using such a wallet.
MetaMask is a popular Ethereum wallet that allows users to manage their digital assets. It provides a simple interface for interacting with the Ethereum blockchain and handles various types of cryptocurrencies.
This wallet enables access to Web3 applications, which are decentralized apps built on blockchain technology. Through MetaMask, users can engage with these dApps directly, promoting a more connected and interactive experience.
MetaMask also supports non-fungible tokens (NFTs). Users can buy, sell, and trade these unique digital assets seamlessly. This capability has made it essential for anyone interested in the NFT market.
Security is a top priority for MetaMask. It generates a seed phrase that acts as a master key to recover access to the wallet, ensuring users can regain control if they forget their password. Additionally, private keys are stored locally on the user’s device, which adds another layer of security.
MetaMask has a user-friendly design, making it suitable for both beginners and experienced users. With over 30 million users, it is recognized as a secure and reliable cryptocurrency wallet. Regular updates and a Bug Bounty program also help the platform stay secure and efficient.
Overall, MetaMask is a versatile tool for anyone navigating the world of Ethereum and decentralized finance.
MetaMask includes various security features that help protect users’ digital assets. These features focus on encryption, regular updates, and privacy measures to enhance security.
Encryption
Encryption is a key element of MetaMask’s security. Users’ private keys are stored locally within their browser and are not sent to MetaMask’s servers. This means that even if the servers were compromised, user data would remain secure.
The application uses strong encryption methods to protect sensitive information. This ensures that only the user can access their wallet with their password. Additionally, when users make transactions, their data is encrypted during transmission, adding another layer of protection against potential threats.
Regular Updates
MetaMask frequently releases updates to improve security and add new features. These updates address known vulnerabilities and ensure that the application complies with the latest security standards.
By regularly updating the software, MetaMask enhances its defenses against emerging threats. Users are encouraged to enable automatic updates to benefit from these improvements without manual intervention. Keeping the application current is vital for maintaining a high level of security for digital assets.
Privacy Measures
MetaMask prioritizes user privacy by not storing personal information on its servers. All sensitive data is encrypted in the user’s browser, meaning MetaMask cannot access private keys or transaction details.
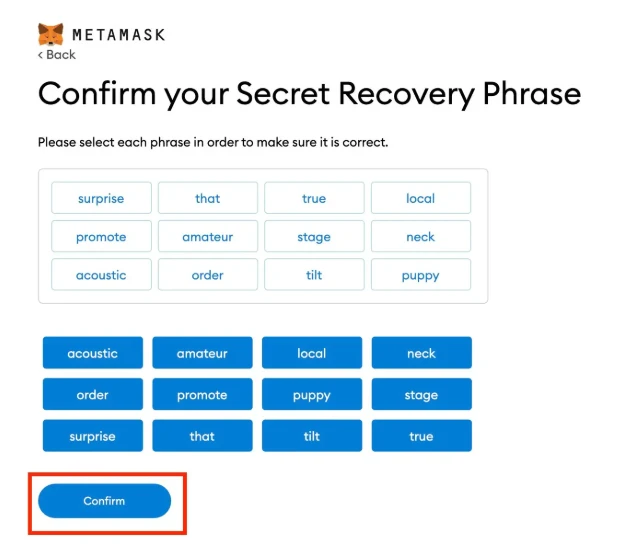
Users can restore their wallet using a unique Secret Recovery Phrase, which they should keep secure. MetaMask also supports in-app token swaps, allowing users to trade without relying on central exchanges, which can be vulnerable to hacks. This feature minimizes the risk of exposing personal information during transactions.
Personal Security Practices
Maintaining personal security is essential for anyone using MetaMask. This includes implementing strong passwords, utilizing two-factor authentication, and being aware of phishing attacks. Each of these practices helps protect users’ digital assets and personal information.
Creating a Strong Password
A strong password is the first line of defense for any online account, including MetaMask. Users should create a password that is at least 12 characters long and includes a mix of uppercase letters, lowercase letters, numbers, and special characters.
Avoid easily guessed information like birthdays or names. It’s also important to use unique passwords for different accounts to reduce risk.
To further enhance security, consider using a password manager. This tool helps manage and generate strong passwords. Users should also change their passwords regularly and back them up securely.
Two-Factor Authentication
Two-factor authentication (2FA) provides an extra layer of security. It requires not only a password but also something that only the user has, like a smartphone. When logging in, the user enters their password and then receives a code via SMS or an authentication app.
This makes it much harder for unauthorized users to access accounts. Users should enable 2FA wherever possible. Even if a password is compromised, the account remains secure if 2FA is activated.
Regularly updating the authentication app and verifying recovery options is also crucial.
Beware of Phishing Attacks
Phishing attacks are a common way for scammers to steal information. Users should be cautious about emails or messages that ask for passwords or personal data. Multiple impersonation attempts can be made, often looking like legitimate sources.
Do not click on suspicious links or download attachments from unknown sources. Always check the sender’s address for legitimacy.
Another safety measure is to directly visit the MetaMask website instead of clicking on links. Regularly updating security settings and being aware of the latest scams can also help users safeguard their information.
Types of Wallets and Features
Different types of cryptocurrency wallets serve unique purposes. Each type offers specific features to meet user needs for safety and convenience.
Hot Wallet versus Cold Wallet
Hot wallets are always connected to the internet. This makes them convenient for daily transactions. Users can access their funds quickly. However, being online means they are more vulnerable to hacks and phishing attacks.
Cold wallets, on the other hand, are offline. They can take the form of hardware wallets or paper wallets. Cold wallets offer increased security since they are less exposed to online threats. They are ideal for long-term storage of cryptocurrency.
For daily usage, hot wallets may be useful. For storing larger amounts, cold wallets are often recommended due to their enhanced security measures.
Hardware Wallet Integration
MetaMask supports integration with hardware wallets like Ledger and Trezor. This feature adds an extra layer of protection for users. Hardware wallets store private keys offline, minimizing the chance of online hacks.
When users link their MetaMask account with a hardware wallet, they combine convenience with security. This integration allows for easy access to funds while still keeping them safe.
Using hardware wallets is a popular practice for those focused on self-custody. It ensures that users control their private keys and digital assets. This method effectively protects against unauthorized access while allowing users to interact with decentralized applications easily.
Proper Management of Your Seed Phrase
Managing a seed phrase correctly is crucial for maintaining security in MetaMask. A seed phrase, also known as a recovery phrase, acts as the key to accessing wallets and funds. If mishandled, it could lead to significant losses.
Backup Best Practices
Backing up the seed phrase is essential. Users should write down their seed phrase on paper and store it in a secure location, like a safe. Digital copies can be risky as malware can target devices.
-
Keep It Private: Never share the seed phrase with anyone.
-
Multiple Copies: Consider making several copies and storing them in different secure locations.
-
Avoid Cloud Storage: Do not save it on cloud services to prevent unauthorized access.
These methods ensure that even if one copy is lost, others remain safe.
Seed Phrase Security
Securing the seed phrase involves multiple layers of protection. Users should be aware that if someone gets hold of the seed phrase, they can access the wallet.
-
Use Security Software: Install anti-malware programs to protect devices from threats.
-
Be Cautious Online: Avoid phishing scams that request personal information related to cryptocurrency wallets.
-
Physical Security: Ensure that the written seed phrase is stored in a place that only trusted individuals can access.
Implementing these strategies will significantly enhance seed phrase security, protecting assets stored in MetaMask.
MetaMask allows users to connect with various decentralized applications, commonly known as dapps. These applications often run on smart contracts, enabling functionality without central control.
-
Install MetaMask: Users should first download and install the MetaMask extension or mobile app. This sets up a wallet to manage digital assets.
-
Create a Wallet: After installation, users must create a wallet by following on-screen instructions. They should secure their seed phrase, as it is crucial for wallet recovery.
-
Connect to a Dapp: When visiting a dapp website, it usually detects if MetaMask is installed. The user may see a prompt to unlock MetaMask. After unlocking, they can refresh the page.
-
Access Decentralized Finance (DeFi): Many dapps focus on DeFi, like Uniswap. Users can swap tokens or provide liquidity by connecting their MetaMask wallet.
-
Manage Permissions: Users should check dapp permissions in MetaMask. They can mark trusted dapps as favorites for easier access in the future.
-
Be Cautious: It is important to recognize potential phishing attempts. Always double-check URLs and ensure they are legitimate before connecting MetaMask.
By following these steps, users can confidently navigate the world of dapps with MetaMask, enjoying the benefits of decentralized finance and smart contracts securely.
Interacting with Different Blockchains
MetaMask is designed to work with multiple blockchains, which allows users to manage various cryptocurrencies easily.
Ethereum and Binance Smart Chain
Ethereum is the most widely used blockchain for decentralized finance (DeFi) applications. It supports smart contracts that enable various functions, such as trading and lending. Users can connect their MetaMask wallet to Ethereum to conduct these activities securely.
Binance Smart Chain (BSC) is another popular option as it offers lower fees and faster transactions compared to Ethereum. Users can also link their MetaMask wallet to BSC easily. This can be done by manually inputting the necessary network details or using tools like Chainlist.
Managing Multiple Cryptocurrencies
Managing different cryptocurrencies in MetaMask requires organization. Users should create separate accounts or wallets for transactions. For example, holding a hot wallet for regular interactions and a cold wallet for more significant, long-term holdings can enhance security.
By using MetaMask, individuals can interact with various DeFi platforms seamlessly. This helps them diversify their investments while keeping track of their assets. Always ensure to double-check network settings before making transactions to avoid costly mistakes.
Metamask is a widely used crypto wallet, trusted by many users worldwide. Safety features are crucial for any wallet, and Metamask has several options in place.
Security Measures:
-
Transaction Confirmation: Metamask requires users to confirm each transaction, helping to prevent unauthorized actions.
-
Recovery Phrase: If a user loses their password, there is a recovery phrase to regain access to the wallet.
-
Regular Updates: Metamask frequently updates its software to fix vulnerabilities and enhance security.
Though Metamask has strong security measures, users must remain vigilant. Phishing attacks are common, and users should be wary of suspicious links and websites.
Users might compare Metamask with other wallets like Trust Wallet and Coinbase Wallet. Ultimately, a lot of the responsibility for security lies with users. They should follow best practices, such as securing their seed phrase and using dedicated devices.
Comparison with Other Wallets
When evaluating the safety of MetaMask, it’s essential to understand how it stacks up against other wallet options. Each type of wallet has unique features and levels of security that cater to different user needs.
MetaMask versus Trust Wallet
MetaMask and Trust Wallet are both popular options among users of decentralized applications. MetaMask is primarily a browser extension and mobile application catering mainly to the Ethereum blockchain. Its user-friendly design makes it convenient for managing tokens and access to dApps.
Trust Wallet supports multiple blockchains beyond Ethereum, making it a versatile choice. Users appreciate its built-in Web3 browser, allowing easy access to decentralized applications.
Key Differences:
-
Supported Blockchains: MetaMask focuses on Ethereum, while Trust Wallet supports numerous cryptocurrencies.
-
User Interface: MetaMask is favored for its simplicity, whereas Trust Wallet offers more features.
-
Security Features: Both wallets allow users to control their private keys, though Trust Wallet can provide an offline storage option.
MetaMask versus Hardware Wallets
Hardware wallets like Ledger and Trezor offer a different level of security compared to MetaMask. They store users’ private keys offline, making them significantly less vulnerable to online threats.
MetaMask is classified as a hot wallet, meaning it is connected to the internet. This connectivity increases accessibility but also introduces potential risks from cyberattacks.
Comparison Points:
-
Security: Hardware wallets provide superior security due to offline storage. MetaMask, while secure, requires users to implement best practices for safety.
-
Convenience: MetaMask is easier to set up and use for quick transactions. Hardware wallets involve extra steps, as users must transfer funds for use.
-
Cost: Hardware wallets require an upfront investment, while MetaMask is free to use.
Both MetaMask and hardware wallets serve specific needs based on user preferences and security requirements.
Troubleshooting Common Issues
When using MetaMask, users may encounter specific technical issues. Understanding how to resolve login problems and transaction failures is crucial for ensuring a smooth experience.
Login Problems
Login issues can arise for several reasons. If users cannot access their wallets, they should first check if they have the correct password. Often, typing errors can lead to problems.
If the password is forgotten, the user can restore their wallet using their seed phrase. It’s essential to keep this phrase secure, as anyone with access can control the wallet.
Additionally, problems may occur due to outdated browser extensions or software. Users should ensure they are using the latest version of MetaMask.
In some cases, malware or phishing attacks can affect login attempts. Keeping antivirus software updated can help prevent these threats. Users need to be cautious of phishing schemes that imitate MetaMask.
Transaction Failures
Transaction failures may occur for various reasons. High network congestion is a common cause. Users should check the current network status to see if there are delays.
If a transaction shows as successful but the received amount is less than expected, users should verify the transaction details on a block explorer. This might help identify issues related to network fees or incorrect addresses.
Another cause could be browser-related problems. Some extensions may conflict with MetaMask, causing disruptions. Users can troubleshoot by disabling other extensions or trying a different browser.
It’s also important to never share sensitive information, such as private keys or seed phrases. Scams and phishing attempts often target this information, leading to significant losses. Being vigilant can help users avoid such issues.
Frequently Asked Questions
What are the security measures implemented by MetaMask to protect users?
MetaMask uses encryption to safeguard private keys and recovery phrases. It also offers features like biometrics and password protection to prevent unauthorized access. Regular updates also help address vulnerabilities.
How does MetaMask ensure safe storage of private keys on mobile devices?
On mobile devices, MetaMask stores private keys locally using secure storage mechanisms. This means the keys are not shared with MetaMask servers, which reduces the risk of exposure.
In what ways can users enhance the security of their MetaMask wallet?
Users can strengthen wallet security by using strong, unique passwords and enabling two-factor authentication (2FA). They should also keep their MetaMask app updated regularly and avoid sharing sensitive information like seed phrases.
What should be done if a user suspects a security breach in their MetaMask wallet?
If a security breach is suspected, the user should immediately disconnect their wallet from all devices and applications. They should transfer their assets to a new wallet and change passwords to secure their accounts.
How does MetaMask compare to other wallets in terms of security?
MetaMask is regarded as a secure option among hot wallets. It provides user-controlled keys and frequent updates but may not offer as high a level of security as cold wallets, which are completely offline.
Are there any known vulnerabilities in MetaMask that users should be aware of?
While MetaMask is generally safe, like any software, it can have vulnerabilities. Users should stay informed about updates and potential issues announced by the MetaMask team to mitigate risks.