CaryptosHeadlines Media Has Launched Its Native Token CHT.
Airdrop Is Live For Everyone, Claim Instant 5000 CHT Tokens Worth Of $50 USDT.
Join the Airdrop at the official website,
CryptosHeadlinesToken.com
CaryptosHeadlines Media Has Launched Its Native Token CHT.
Airdrop Is Live For Everyone, Claim Instant 5000 CHT Tokens Worth Of $50 USDT.
Join the Airdrop at the official website,
CryptosHeadlinesToken.com
Meme coin scams on X are not the only scams crypto users are trying to avoid. Sensitive attendee data from crypto events is being sold online, fueling concerns about targeted phishing and social engineering attacks. Bait wallet schemes are also tricking greedy users into sending funds to multisignature wallets, ensuring scammers yield some impressive profits. Meanwhile, the FBI and other law enforcement agencies linked the $300 million theft from Japan’s DMM exchange to the North Korean TraderTraitor group, which it achieved by using very sophisticated social engineering techniques.
Hackers Take Advantage of Meme Coin Hype
A sophisticated phishing scam netted a threat actor close to $500,000 over the past month by targeting 15 compromised X accounts, according to blockchain investigator ZachXBT. The attacker reportedly impersonated the X team, and sent fake copyright infringement notices to lure users into visiting phishing sites. These sites tricked victims into providing credentials to reset their X account passwords and disable two-factor authentication (2FA), which allowed the perpetrator to gain control of the accounts.
Many of the compromised accounts were crypto-focused and included names like Kick, Cursor, The Arena, Brett, and Alex Blania, and they were used to promote meme coin scams. The phishing scheme involved six deployer addresses to launch various scams, with stolen funds being moved between the Solana and Ethereum networks in an attempt to obscure the source of the transactions. ZachXBT advised users to avoid reusing email addresses across services and to enable 2FA on critical accounts to boost security.
The first incident was reported on Nov. 26 with RuneMine’s account, while the latest involved Kick on Dec. 24. Many of these accounts had large followings of more than 200,000 users, particularly in the meme coin community. Posts from compromised accounts often used captions like “Incoming Transmission” to announce fraudulent tokens and contract addresses. Some of the affected accounts, like the cross-chain scalability platform Neutron, have publicly acknowledged the attacks.
This surge in phishing activity comes as crypto scammers seem to be trying to recover losses after phishing incidents dropped 53% month-on-month in November. However, 2024 has seen a rise in crypto theft, with blockchain forensics firm Chainalysis reporting $2.2 billion stolen across 303 major incidents—a 21% increase from the previous year.
Scammers Use Bait Wallets to Trap Greedy Crypto Thieves
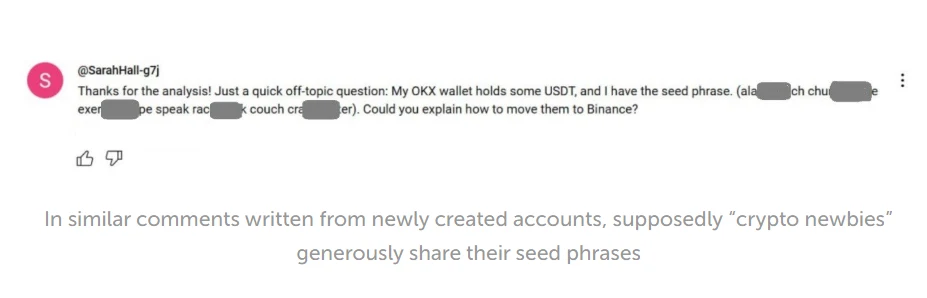
A new crypto scam also recently emerged where fraudsters pose as inexperienced users by sharing the seed phrase of a wallet supposedly filled with funds, luring people into a trap that is designed to steal their crypto instead. According to a Dec. 23 blog post by Kaspersky analyst Mikhail Sytnik, scammers are targeting finance-related YouTube videos by posting comments with seed phrases under the guise of asking for help transferring Tether (USDT) funds.
(Source: Kaspersky)
One such wallet seen by Sytnik contained $8,000 in USDT on the Tron network as bait. To transfer the funds, potential thieves would need to send Tron (TRX), the blockchain’s native token, to cover network fees. However, the bait wallet is set up as a multisignature wallet requiring multiple approvals for outgoing transactions. As soon as TRX is sent to the wallet, the funds are immediately transferred to another wallet controlled by the scammers. This setup ensures that even after paying the fees, the USDT cannot be transferred by the would-be thief.
Sytnik compared the scammers to digital Robin Hoods, and he advised users never to try accessing others’ wallets, even if provided with a seed phrase, and to remain cautious about claims from strangers online regarding cryptocurrency.
This tactic is the latest in a series of scams that are designed to exploit greed in the crypto community. In July, Kaspersky uncovered an even more elaborate scheme involving Telegram links that led victims to legitimate-looking crypto exchanges, only to infect their devices with malware capable of stealing extensive data and assets.
Crypto Event Data Leaks Spark Security Concerns
Meanwhile, lists containing sensitive information about crypto industry event attendees are being sold online, and are posing serious risks for targeted scams and malicious activities. These lists are marketed as tools for “marketing and promoting and finding clients,” and include personal details like names, phone numbers, nationalities, job roles, companies, and social media profiles. Some even extend to ticket purchase data, operating systems used, follower counts, crypto wallet addresses, and messages sent to event organizers.
The data seems to be gathered through event registration forms, particularly at conferences and side events using platforms like lu.ma, which often require social media account links. The events primarily took place in Southeast Asia and India during the fall of 2024, which suggests an organized international trade rather than isolated incidents.
Sample of one list shared
One sample included a list of 1,700 attendees from the AIBC conference in Malta, initially priced at $4,000 but later reduced to $650. The seller claimed the proceeds would be used to buy more lists from events like Coinfest and DevCon. Analysis suggests that the seller and data compiler may be Russian, based on certain language clues and AI assessments of their communication.
While the seller argued that the data was not sensitive and that attendees might welcome marketing efforts, cybersecurity experts still warn that this information could facilitate social engineering scams and phishing attempts. AIBC founder Eman Pulis stated that the event has strict protocols against data breaches and pointed out that fraudulent databases are common in the industry.
Although the source of the data is still unclear, it is evident that these lists are in demand among bad actors.
FBI Links $300M Crypto Theft to TraderTraitor Group
The U.S. Federal Bureau of Investigation (FBI), along with the Department of Defense Cyber Crime Center (DC3) and Japan’s National Police Agency (NPA), recently shared details about how North Korean-linked hackers stole more than $300 million from the Japanese crypto exchange DMM in May. The theft involved 4,502.9 Bitcoin, valued at close to $305 million at the time of the hack.
The FBI attributed the attack to the North Korean group TraderTraitor, which uses advanced social engineering techniques. In March, a North Korean hacker posed as a recruiter on LinkedIn, targeting an employee at Ginco, a Japan-based crypto wallet company. The hacker sent a malicious GitHub link disguised as a pre-employment test, which the employee copied to their personal GitHub account, compromising their access.
After using the stolen credentials, the hackers infiltrated Ginco’s communications system in May and impersonated the compromised employee. They then manipulated a legitimate transaction request made by a DMM employee, which resulted in the theft of more than $300 million in Bitcoin. The stolen funds were transferred to wallets controlled by the TraderTraitor group.