A new phishing campaign is reportedly targeting Ledger hardware wallet users through fake data breach notification emails.
Security researchers at BleepingComputer reported that scammers are sending emails that appear to come from Ledger’s official support address to users. According to them, the message claims users must verify their recovery phrases due to a security breach.
The scam reportedly began on December 15, 2024, and uses Amazon AWS infrastructure to appear legitimate. These phishing attempts are designed to steal users’ 24-word recovery phrases, which would give attackers complete access to victims’ cryptocurrency funds.
The campaign appears to be particularly effective because it exploits real concerns stemming from Ledger’s previous 2020 data breach, an episode when customer information was actually exposed.
Crypto phishing campaign appears official
The fraudulent emails follow a careful pattern designed to appear official. They arrive with the subject line “Security Alert: Data Breach May Expose Your Recovery Phrase” and appear to come from “Ledger [email protected].” However, investigators found that scammers are actually using the SendGrid email marketing platform to distribute these messages.
When users click the “Verify My Recovery Phrase” button in these emails, they are redirected through multiple stages. The first redirect leads to an Amazon AWS website at a suspicious URL: product-ledg.s3.us-west-1.amazonaws.com. From there, users are sent to a phishing site.
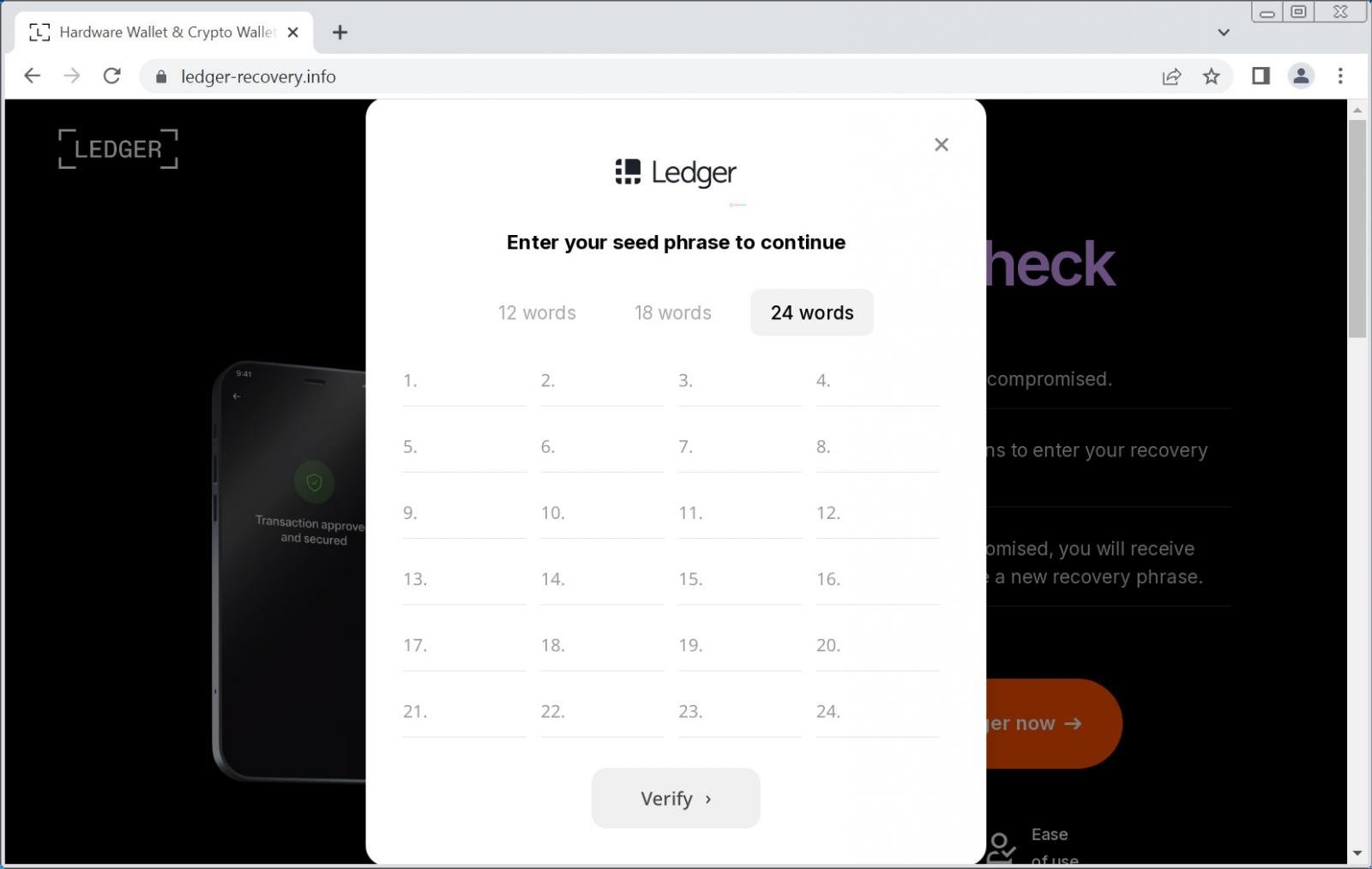
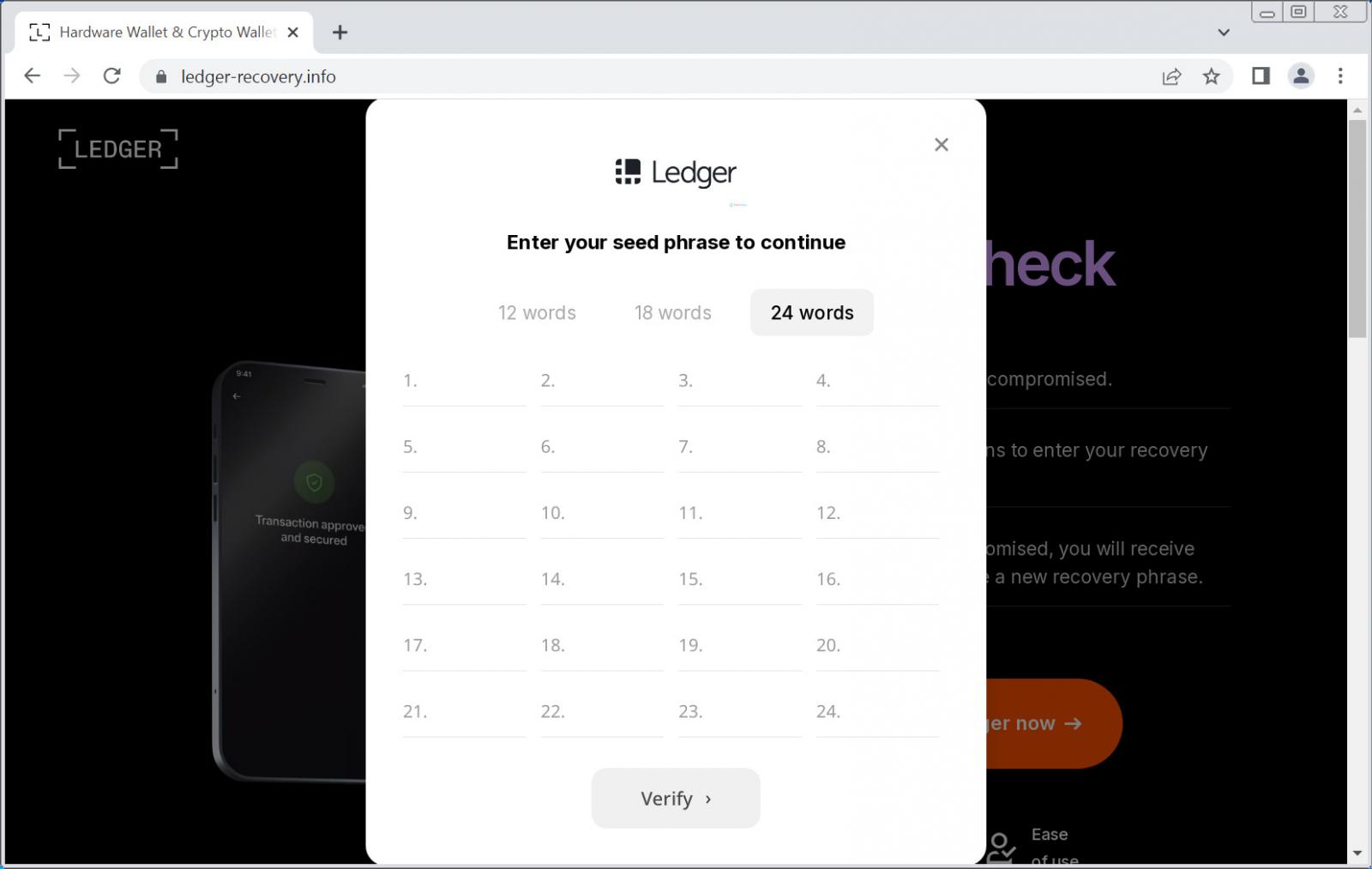
The phishing website shows clear technical capabilities. It includes a verification system that checks each entered word against the 2,048 valid words used in cryptocurrency recovery phrases. This real-time validation makes the site appear more legitimate to victims.
The attackers also added another deceptive element: the site always claims the entered phrase is invalid to encourage multiple attempts and to probably doublecheck that they received the correct recovery words.
Additional versions of this scam have also been identified. Some emails claim to be firmware update notifications, but they share the same goal of stealing users’ recovery phrases to gain access to their cryptocurrency wallets. Each entered word is transmitted immediately to the attackers’ servers.
Ledger has issued several security reminders
Ledger has since issued several security reminders in response to this phishing campaign. The company emphasizes that it will never request recovery phrases through email, websites, or any other means.
Some security recommendations shared since then have reminded users that the only legitimate use of a recovery phrase is during the initial setup of a new hardware wallet or when recovering access to an existing wallet – and these actions should only be performed on the physical Ledger device itself.
Security recommendations for users to protect themselves have also reminded them to always type Ledger’s web address (ledger.com) directly into the browser rather than clicking email links.
Second, users were advised to treat any email claiming to be from Ledger with extreme caution, especially those mentioning data breaches or requiring immediate action. Third, users were reminded about offline storage of recovery phrases, preferably in a secure physical location away from digital devices.
For those who may have already interacted with suspicious emails or websites, they advised immediate action. Users who entered their recovery phrase into any website should transfer their funds to a new wallet with a fresh recovery phrase immediately. The original wallet should be considered compromised and should no longer be used for storing cryptocurrency.
A Step-By-Step System To Launching Your Web3 Career and Landing High-Paying Crypto Jobs in 90 Days.